Privileged Access Management
Paraview Privileged Access Management (PAM) protects your organization against attacks, meet Audit & Compliance Standards, and empower your digital business.

Key Functions
Efficient Privileged Credential Management
Effortlessly handle privileged credentials with automatic discovery and onboarding of credentials used by both human and non-human identities. Centralized policy management empowers administrators to define policies for password complexity, rotation frequency, user access privileges, and more. Automated password rotation enhances security while alleviating the IT team's manual workload.
Isolation and Session Monitoring
Stay compliant by recording essential events and maintaining tamper-resistant audit logs. Create secure, isolated remote sessions and record all activities. End users never have direct connections to target systems, reducing the risk of malware. Session recordings are securely and centrally stored, simplifying accountability and compliance for security and audit purposes.
Remote PAM Access
Facilitate secure remote access for employees and external vendors to Privileged Access Manager, regardless of their location. Achieve this without the need for VPNs or agents, and eliminate passwords for enhanced security.
Adaptive MFA & SSO
Ensure the validation of privileged users with context-aware Adaptive Multi-Factor Authentication while providing secure access to business resources through Single Sign-On.
Efficient Privileged Credential Management
Effortlessly handle privileged credentials with automatic discovery and onboarding of credentials used by both human and non-human identities. Centralized policy management empowers administrators to define policies for password complexity, rotation frequency, user access privileges, and more. Automated password rotation enhances security while alleviating the IT team's manual workload.
Isolation and Session Monitoring
Stay compliant by recording essential events and maintaining tamper-resistant audit logs. Create secure, isolated remote sessions and record all activities. End users never have direct connections to target systems, reducing the risk of malware. Session recordings are securely and centrally stored, simplifying accountability and compliance for security and audit purposes.
Remote PAM Access
Facilitate secure remote access for employees and external vendors to Privileged Access Manager, regardless of their location. Achieve this without the need for VPNs or agents, and eliminate passwords for enhanced security.
Adaptive MFA & SSO
Ensure the validation of privileged users with context-aware Adaptive Multi-Factor Authentication while providing secure access to business resources through Single Sign-On.
Efficient Privileged Credential Management
Effortlessly handle privileged credentials with automatic discovery and onboarding of credentials used by both human and non-human identities. Centralized policy management empowers administrators to define policies for password complexity, rotation frequency, user access privileges, and more. Automated password rotation enhances security while alleviating the IT team's manual workload.
Isolation and Session Monitoring
Stay compliant by recording essential events and maintaining tamper-resistant audit logs. Create secure, isolated remote sessions and record all activities. End users never have direct connections to target systems, reducing the risk of malware. Session recordings are securely and centrally stored, simplifying accountability and compliance for security and audit purposes.
Remote PAM Access
Facilitate secure remote access for employees and external vendors to Privileged Access Manager, regardless of their location. Achieve this without the need for VPNs or agents, and eliminate passwords for enhanced security.
Adaptive MFA & SSO
Ensure the validation of privileged users with context-aware Adaptive Multi-Factor Authentication while providing secure access to business resources through Single Sign-On.
Product Technology Features
Secure storage of privileged credentials in an encrypted vault, ensuring that passwords, SSH keys, and other sensitive data are inaccessible to unauthorized users. Reduces the risk of credential theft and misuse.
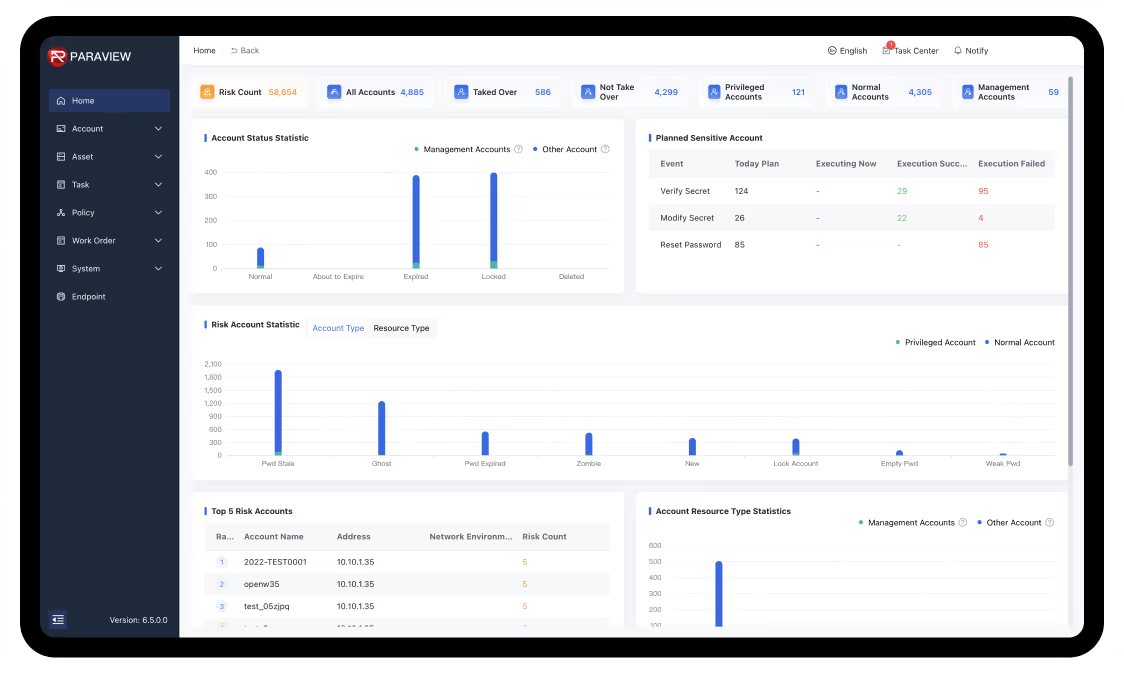
Real-time monitoring and recording of privileged sessions, allowing organizations to track and audit user activities. Helps in compliance with regulations and provides a forensic trail in case of security incidents.

Allows the definition of fine-grained access policies, specifying who can access what resources, when, and under what conditions. Enhances security by enforcing the principle of least privilege.


Use Cases
Use Cases
Securing Administrative Accounts
Administrators and IT staff require elevated privileges to manage systems, networks, and applications. Paraview PAM ensures that these administrative accounts are secured, and access is granted only to authorized personnel. Prevents unauthorized access and misuse of administrative credentials, reducing the risk of insider threats and external attacks.
Third-Party Vendor Access
Organizations often allow third-party vendors to access their systems for maintenance, support, or development. Paraview PAM manages and monitors their access, ensuring vendors only have the permissions necessary to complete their tasks. Reduces the risk of third-party breaches by providing controlled, time-limited access to external users.
Compliance and Regulatory Requirements
Many industries, such as finance, healthcare, and government, are subject to strict regulatory requirements for access control and data protection. Paraview PAM helps organizations meet these requirements by providing detailed audit logs and reports on privileged access activities. Simplifies compliance with regulations like GDPR, HIPAA, SOX, and PCI-DSS, reducing the risk of non-compliance penalties.
Securing DevOps Environments
In DevOps environments, developers and operations teams often require elevated access to automate deployments, manage infrastructure, and access critical systems. Paraview PAM manages and secures these access, integrating with CI/CD pipelines and automation tools. Ensures that only authorized users and processes can access sensitive environments, reducing the risk of breaches and maintaining the integrity of the DevOps pipeline.
Business Benefits
Protecting Against Attacks
Protect your organization from attacks by securing privileged identities—both human and machine—in a tamper-resistant operational environment.
Meeting Audit & Compliance Standards
Fulfill internal requirements, oversee access, and maintain a centralized audit trail to ensure compliance with industry standards.
Empowering the Digital Business
Facilitate secure user authentication with VPN-less access through a single web portal, enabling your digital business to thrive.
Related Case Studies
Ready to Embrace a Safe and Efficient Digital World?
Contact us and Let’s discuss how Paraview can secure your identity and API assets.

